Exercise 3.7: GSM System Components
From LNTwww
See also "Exercise 3.2Z"
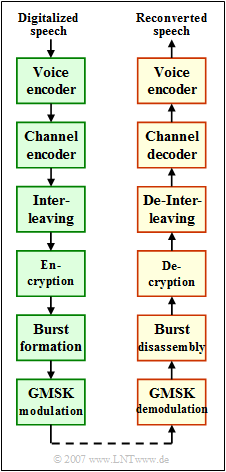
The diagram shows the entire GSM transmission path, with the transmitter on the left and the receiver on the right. The illustration refers only to voice transmission. In GSM data transmission, only the top block (voice encoder or decoder) is replaced by another channel encoder or decoder (concatenation of two channel codes).
The two respective lowest system components were already treated in detail in the exercises for the chapter "Radio Interface" .
In this exercise, on the other hand, some basic properties are queried from.
- Speech encoders and speech decoders,
- convolutional encoder and convolutional decoder,
- interleaver and de-interleaver, and
- encryption and decryption.
Hint:
- This exercise belongs to the chapter "Entire GSM Transmission System".
Questions
Solution
(1) Correct are answers 1 and 4:
- The goal of speech coding is data compression and thus redundancy reduction.
- This is a typical task of source coding.
(2) Correct are answers 2 and 3:
- Convolutional coding is a form of channel coding by which the receiver (convolutional decoder) is enabled to detect and possibly correct errors.
- The channel coder adds (meaningful) redundancy for this purpose, while the speech coder removes irrelevant redundancy.
- Often both components are implemented together or at least closely coordinated.
- This is then referred to as "joint source– and channel coding".
(3) Only answer 2 is correct:
- The convolutional decoder has major problems when the transmission errors are clustered rather than statistically independent.
- The task of interleavers and de-interleavers is to break up such bunching errors and spread them over a larger period of time.
- The redundancy is not changed by this procedure.
- In the AWGN channel, bit errors occur statistically independently, so interleaver and de-interleaver can be omitted.
(4) Correct are answers 1 and 4:
- Encryption and decryption - the counterpart on the receiving side - are used solely to protect user data from unauthorized access.
- They are not used for error correction, nor do they add redundancy.
- A distinction is made between symmetric and asymmetric encryption. GSM predominantly uses the first variant.