Difference between revisions of "Examples of Communication Systems/General Description of UMTS"
| (15 intermediate revisions by 2 users not shown) | |||
| Line 14: | Line 14: | ||
⇒ In 2011 $($when this chapter was conceived$)$ about 200 million subscribers worldwide were using UMTS or similar third-generation mobile communications systems. | ⇒ In 2011 $($when this chapter was conceived$)$ about 200 million subscribers worldwide were using UMTS or similar third-generation mobile communications systems. | ||
| − | ⇒ In 2022 $($when this chapter was revised again as part of the English translation$)$ a global report by the network equipment industry has identified more than hundred operators that have either completed 3G switch-off alongside 2G switch-off, are planning to do so or are in the process of doing so, in order to use the spectrum this frees up for [[Mobile_Communications/General_Information_on_the_LTE_Mobile_Communications_Standard| " | + | ⇒ In 2022 $($when this chapter was revised again as part of the English translation$)$ a global report by the network equipment industry has identified more than hundred operators that have either completed 3G switch-off alongside 2G switch-off, are planning to do so or are in the process of doing so, in order to use the spectrum this frees up for [[Mobile_Communications/General_Information_on_the_LTE_Mobile_Communications_Standard| "LTE"]], "5G" or technology-neutral. |
*28 operators in 17 countries and territories have now completed 3G switch-off. | *28 operators in 17 countries and territories have now completed 3G switch-off. | ||
| Line 22: | Line 22: | ||
*Another 46 operators in 31 countries have 3G shutdowns planned for the very near future. | *Another 46 operators in 31 countries have 3G shutdowns planned for the very near future. | ||
| − | *It is also interesting to note from this report that in some countries the UMTS switch-off is being pushed even harder than that of the 2G standard [[Examples_of_Communication_Systems/General_Description_of_GSM| " | + | *It is also interesting to note from this report that in some countries the UMTS switch-off is being pushed even harder than that of the 2G standard [[Examples_of_Communication_Systems/General_Description_of_GSM| "GSM"]], which is about ten years older. |
| − | ⇒ We have chosen to keep this chapter in our $\rm LNTwww$ despite this negative forecast, since understanding the underlying CDMA technology also facilitates students' understanding of other communications engineering problems | + | ⇒ We have chosen to keep this chapter in our $\rm LNTwww$ despite this negative forecast, since understanding the underlying CDMA technology also facilitates students' understanding of other communications engineering problems. |
This chapter includes in detail: | This chapter includes in detail: | ||
| − | #»UMTS | + | #»UMTS« as a third-generation mobile communications system, |
#the »services and security aspects« in UMTS, | #the »services and security aspects« in UMTS, | ||
#the »UMTS network architecture«, | #the »UMTS network architecture«, | ||
| Line 201: | Line 201: | ||
In the UMTS radio channel, in addition to interference from other subscribers and noise, a number of unpredictable, interfering and distorting effects occur, which also change over time. | In the UMTS radio channel, in addition to interference from other subscribers and noise, a number of unpredictable, interfering and distorting effects occur, which also change over time. | ||
| − | [[File: | + | [[File:EN_Mob_T1_1_S1.png|right|frame|Example for a mobile radio scenario|class=fit]] |
| − | Due to reflections as well as scattering and diffraction from objects, the transmitted signal experiences multipath | + | ⇒ Due to reflections as well as scattering and diffraction from objects, the transmitted signal experiences '''»multipath propagation«'''. |
| − | *The signal reaches the receiver not only via the direct path, but via several paths with different propagation times and different attenuation. | + | *The signal reaches the receiver not only via the direct path, but via several paths with different propagation times and different attenuation. |
| − | *The multipath scattering is influenced by the environment, but additionally also by a possible movement of the | + | |
| − | + | *The multipath scattering is influenced by the environment, but additionally also by a possible movement of the user, as indicated in the graph by the movement speed $v$. | |
| − | The '''path loss''' goes back to propagation properties of electromagnetic waves | + | |
| − | *The received power of a radio signal decreases with distance $d$ by $d^{-γ}$, where $γ$ is a medium-dependent constant of the radio propagation wave. | + | |
| − | *Accounting for constructive or destructive ground reflections, the constant $γ$ below the "break point" $d_0$ takes values between $2$ and $3$ | + | ⇒ The '''path loss''' goes back to propagation properties of electromagnetic waves – see page [[Mobile_Communications/Distance_Dependent_Attenuation_and_Shading#Common_path_loss_model|"common path loss model"]] in the book "Mobile Communication". For the study of this attenuation phenomenon, we assume a simplified path loss model. This states: |
| − | *Above this characteristic point, the reflection effects increase and the propagation constant $γ$ grows to values between $3.5$ and $4$ | + | *The received power of a radio signal decreases with distance $d$ by $d^{-γ}$, where $γ$ is a medium-dependent constant of the radio propagation wave. |
| + | |||
| + | *Accounting for constructive or destructive ground reflections, the constant $γ$ below the "break point" $d_0$ takes values between $2$ and $3$. | ||
| + | |||
| + | *Above this characteristic point, the reflection effects increase and the propagation constant $γ$ grows to values between $3.5$ and $4$. | ||
| − | + | {{GraueBox|TEXT= | |
| − | {{GraueBox|TEXT= | ||
$\text{Example 1:}$ | $\text{Example 1:}$ | ||
| − | Shown on the right is the path loss (in dB) as a function of distance $d$. In this example, the constant $α_0 = 10^{-5}$ | + | Shown on the right is the path loss $($in dB$)$ as a function of the distance $d$ $($in meter$)$. |
| − | + | [[File:EN_Bei_T_4_1_S2_neu.png|right|frame|Path loss $($attenuation$)$ as a function of the distance]] | |
| − | + | In this example, | |
| − | + | *the constant $α_0 = 10^{-5}$ is set ⇒ $10 \cdot \lg \ α_0 = 50 \ \rm dB$, | |
| + | |||
| + | *the break point is at $d_0 = \ \rm 100 \ m$. | ||
| + | |||
| + | |||
| + | |||
| + | |||
| + | |||
| + | |||
| + | |||
| + | |||
| + | One can see from the graph: | ||
| + | #In the left-hand range $(d \ll d_0)$ holds $γ \approx 2$<br><br> | ||
| + | #For $d \gg d_0$ on the other hand: $γ \approx 4$.<br><br> | ||
| + | #In the region around $d = d_0$: <br>The propagation constant increases continuously from $γ = 2$ to $γ = 4$. }} | ||
| − | ==Frequency– and time–selective fading== | + | ==Frequency–selective and time–selective fading== |
<br> | <br> | ||
| − | An essential property of the mobile radio channel is the so-called '''fading''' | + | An essential property of the mobile radio channel is the so-called '''»fading«'''. This is caused by time-varying shadowing and by possible movements of the mobile subscriber. In the book "[[Mobile_Communications/Probability_Density_of_Rayleigh_Fading#Frequency-selective_fading_vs._non-frequency-selective_fading|Mobile Communications]]" this type of signal degradation is discussed in detail. |
| − | + | Here follows only a brief summary. One distinguishes on the one hand: | |
| + | *'''»Short term fading«''' or "fast fading" ⇒ short term drops in the received power $($mostly in the microseconds range$)$. | ||
| − | + | *'''»Long term fading«''' or "slow fading" ⇒ only slow changes $($mostly in the seconds range$)$. | |
| − | *'' | ||
| − | |||
| + | ::Fast fading mainly affects systems with large symbol durations, i.e. small bandwidths. However, since the bandwidth of UMTS is much larger than that of GSM, this system is less susceptible to fast fading. | ||
| − | + | Furthermore, fading can also be classified as follows: | |
| + | *'''»Frequency-selective fading«''' is caused by multipath propagation over paths with different delay times. <br> As a result of this fading, different frequency components are attenuated differently by the power transfer function $|H_{\rm K}(f)|^2$ of the channel. | ||
| − | + | *'''»Time-selective fading«''' occurs due to a relative motion between transmitter and receiver. <br> This causes frequency shifts depending on the direction of movement $($towards or away from the transmitter$)$ which are physically described by the [[Mobile_Communications/Statistical_Bindings_within_the_Rayleigh_Process#Phenomenological_description_of_the_Doppler_effect|"Doppler effect"]]. | |
| − | * | ||
| − | |||
| + | ::The fading characteristics "frequency selective" and "time selective" shall now be explained in more detail, in particular it will be explained under which conditions which of these fading types are to be expected. At this point we also refer to two e-learning tools: | ||
| + | ::# HTML5/JavaScript applet [[Applets:The_Doppler_Effect|"The Doppler effect"]], | ||
| + | ::# German language SWF applet [[Applets:Multipath_propagation_and_frequency_selectivity_(Applet)|"Multipath propagation and frequency selectivity"]]. | ||
| − | + | {{BlaueBox|TEXT= | |
| − | + | $\text{Characteristics of frequency-selective fading:}$ | |
| − | + | *Receiving different scattering components with different delay times results in a '''»delay spread«''' $T_{\rm V}$, defined as the difference between maximum and minimum delay times $($ German: "Verzögerungszeiten ⇒ subscript "V"$)$. The inverse of this gives approximately the '''»coherence bandwidth«''' $B_{\rm K}$. | |
| − | + | *It is called "frequency-selective fading" if the coherence bandwidth $B_{\rm K}$ is much smaller than the signal bandwidth $B_{\rm S}$. As a result, different frequency components are attenuated differently by the channel, resulting in linear distortions.}} | |
| − | |||
| − | |||
| − | *It is called | ||
{{BlueBox|TEXT= | {{BlueBox|TEXT= | ||
$\text{Characteristics of time-selective fading:}$ | $\text{Characteristics of time-selective fading:}$ | ||
| − | *In time-selective fading, a so-called '''Doppler spread''' $B_{\rm D}$ occurs, which is defined as the difference between | + | *In "time-selective fading", a so-called '''»Doppler spread«''' $B_{\rm D}$» occurs, which is defined as the difference between maximum and minimum Doppler frequencies. |
| − | *The reciprocal of which is called the | + | |
| + | *The reciprocal of which is called the "correlation time" $T_{\rm D} = {1}/{B_{\rm D} }$. In some literatures, this quantity is also referred to as "coherence time". In UMTS, "time-selective fading" occurs whenever the correlation time $T_{\rm D}$ is much smaller than the chip duration $T_{\rm C}$.}} | ||
{{GraueBox|TEXT= | {{GraueBox|TEXT= | ||
$\text{Example 2:}$ | $\text{Example 2:}$ | ||
| − | The left graph illustrates the difference between frequency selective and non-frequency selective fading: | + | The left graph illustrates the difference between frequency-selective and non-frequency-selective fading: |
| − | [[File: | + | [[File:EN_Bei_T_4_1_S7_v3.png|right|frame|The red curves illustrate frequency-selective and time-selective fading]] |
| − | + | #Shown in this graph is the logarithm power transfer function $\vert H_{\rm K}(f,\ t)\vert ^2$ of the channel at a fixed time $t$. | |
| − | + | #While non-frequency-selective fading is plotted in blue with $-5 \ \rm dB$ , the red curve shows an example of frequency-selective fading. | |
| − | + | #Different frequency components are thereby attenuated differently. | |
| − | The right graph schematically | + | The right graph shows schematically "time-selective fading": |
| − | + | #Here, the power transfer function $\vert H_{\rm K}(f,\ t) \vert ^2$ of the channel for a fixed frequency $f$ is plotted. | |
| − | + | #The blue curve is valid for non-time-selective fading: At any time the signal is attenuated by $5 \rm dB$ . }} | |
==UMTS services == | ==UMTS services == | ||
<br> | <br> | ||
| − | One of the goals of the introduction of UMTS is to expand and diversify the mobile communications services offered. A UMTS | + | One of the goals of the introduction of UMTS is to expand and diversify the mobile communications services offered. A UMTS capable terminal must support a number of more complex multimedia applications and functions in addition to the classic services $($speech transmission, messaging, ...$)$. |
| − | These services can be divided into six main categories, depending on the application: | + | These services can be divided into six main categories, depending on the application: |
| − | + | #'''Information''' : Internet surfing $($info-on-demand$)$, online print media, | |
| − | + | #'''Communication''': Video and audio conferencing, fax, ISDN, messaging, | |
| − | + | #'''Entertainment''': Mobile TV, mobile radio, video-on-demand, online gaming, | |
| − | + | #'''Business''': Interactive shopping, e-commerce, | |
| − | + | #'''Technical area''': Online support, distribution service $($speech and data$)$, | |
| − | + | #'''Medical area''': Telemedicine. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
==Security aspects== | ==Security aspects== | ||
<br> | <br> | ||
| − | The security features in UMTS networks are based on the same principles as in GSM. However, some GSM security features have been removed, replaced or expanded. This has made | + | The security features in UMTS networks are based on the same principles as in GSM. However, some GSM security features have been removed, replaced or expanded. |
| − | + | ||
| − | + | This has made | |
| − | + | #the encryption algorithms more robust, | |
| + | #the authentication algorithms more stringent, and | ||
| + | #the subscriber confidentiality criteria tighter. | ||
The main security standards adopted from GSM in UMTS are: | The main security standards adopted from GSM in UMTS are: | ||
| − | # | + | # subscriber authentication, |
| − | # | + | # confidentiality of the subscriber identity, |
| − | # | + | # encryption of the radio interface. |
In addition to these, other security measures have been observed in UMTS: | In addition to these, other security measures have been observed in UMTS: | ||
# Mutual authentication to avoid the use of false base stations, | # Mutual authentication to avoid the use of false base stations, | ||
| − | # | + | # encryption of the connection between base station and associated control node, |
| − | # | + | # encryption and authentication of security data during transmission, |
| − | # | + | # mechanisms for updating the security features. |
| + | [[File:EN_Bei_T_4_1_S10_v2.png|right|frame|Compilation of security measures in UMTS]] | ||
| + | |||
| + | |||
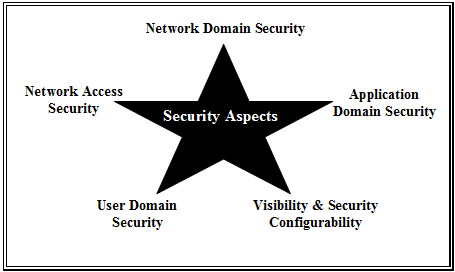
| + | One can classify the above security measures according to the graph. A distinction is made between security concepts for | ||
| + | *the '''»Network Access Security«''' for each subscriber, | ||
| − | + | *the '''»User Domain Security «''' – access to terminal equipment is ensured, | |
| − | + | *the '''»Network Domain Security«''' – a secure exchange of control data between nodes within the network domain is ensured, | |
| − | |||
| − | *the '''Network | ||
| − | *the ''' | + | *the '''»Application Domain Security«''' – the secure exchange between applications of the subscriber terminals and the network providers is guaranteed. |
| − | + | ||
| − | + | The UMTS subscriber can see at any time which of these security measures are in operation and which of them are required for specific services. In this context, one speaks of "Visibility and Configurability Security". | |
| − | |||
| − | The UMTS subscriber can see at any time which of these security measures are in operation and which of them are required for specific services. In this context, one speaks of | ||
==Exercises for the chapter== | ==Exercises for the chapter== | ||
<br> | <br> | ||
| − | [[Aufgaben:Exercise_4.1:_Different_Duplex_Methods_for_UMTS| | + | [[Aufgaben:Exercise_4.1:_Different_Duplex_Methods_for_UMTS|Exercise 4.1: Different Duplex Methods for UMTS]] |
| − | [[Aufgaben:Exercise_4.2:_UMTS_Radio_Channel_Basics| | + | [[Aufgaben:Exercise_4.2:_UMTS_Radio_Channel_Basics|Exercise 4.2: UMTS Radio Channel Basics]] |
{{Display}} | {{Display}} | ||
Latest revision as of 14:00, 13 March 2023
Contents
- 1 # OVERVIEW OF THE FOURTH MAIN CHAPTER #
- 2 Requirements for third–generation mobile communications systems
- 3 The IMT–2000 standard
- 4 Historical development of UMTS
- 5 Frequency allocation for UMTS
- 6 Full duplex
- 7 Properties of the UMTS radio channel
- 8 Frequency–selective and time–selective fading
- 9 UMTS services
- 10 Security aspects
- 11 Exercises for the chapter
# OVERVIEW OF THE FOURTH MAIN CHAPTER #
$\rm U$niversal $\rm M$obile $\rm T$elecommunications $\rm S$ystem $\rm (UMTS)$ is a third-generation mobile communications system, which, when it was introduced, was intended to be a forward-looking alternative to the mobile communications systems used until then. Compared with GSM, UMTS not only offers higher-quality speech, but also a variety of enhanced services and functionalities thanks to its faster and packet-switched transmission.
UMTS was standardized in the late 1990s as part of a collaboration between the "International Telecommunication Union" $\rm (ITU)$ and the 3GPP Forum $($"3rd Generation Partnership Project"$)$ and has been commercially available in Europe since 2004.
⇒ In 2011 $($when this chapter was conceived$)$ about 200 million subscribers worldwide were using UMTS or similar third-generation mobile communications systems.
⇒ In 2022 $($when this chapter was revised again as part of the English translation$)$ a global report by the network equipment industry has identified more than hundred operators that have either completed 3G switch-off alongside 2G switch-off, are planning to do so or are in the process of doing so, in order to use the spectrum this frees up for "LTE", "5G" or technology-neutral.
- 28 operators in 17 countries and territories have now completed 3G switch-off.
- Six operators in six countries and territories currently have 3G switch-off underway.
- Another 46 operators in 31 countries have 3G shutdowns planned for the very near future.
- It is also interesting to note from this report that in some countries the UMTS switch-off is being pushed even harder than that of the 2G standard "GSM", which is about ten years older.
⇒ We have chosen to keep this chapter in our $\rm LNTwww$ despite this negative forecast, since understanding the underlying CDMA technology also facilitates students' understanding of other communications engineering problems.
This chapter includes in detail:
- »UMTS« as a third-generation mobile communications system,
- the »services and security aspects« in UMTS,
- the »UMTS network architecture«,
- the »physical, logical and transport channels« and their interactions,
- the »cellular architecture in UMTS« and its mechanisms,
- the »speech and channel coding« used in UMTS,
- the »band spreading and CDMA« as the basis of UMTS,
- the »radio resource management and power control« in UMTS networks,
- the »further developments of UMTS« such as »HSDPA« and »HSUPA«,
- an outlook on »Long Term Evolution« $\rm (LTE)$, the buzzword of the fourth generation.
Requirements for third–generation mobile communications systems
The main motivation for the development of »third-generation mobile communications systems« was the realization that second-generation systems could not satisfy the bandwidth requirements for the use of multimedia services.
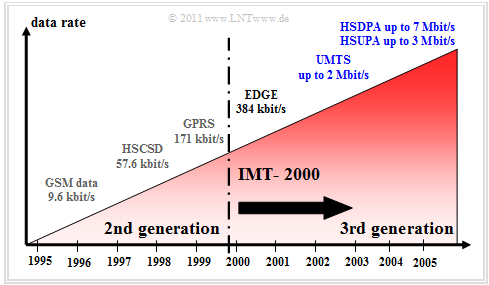
The graph shows the development of mobile radio systems since 1995 in terms of performance or data transmission rate as seen in 2007:
- The specified data rates for HSUPA $($uplink, up to $\text{3 Mbit/s)}$ and HSDPA $($downlink, up to $\text{7 Mbit/s)}$ were realistic for 2006/2007.
- In contrast, the specifications stated maximum values for the uplink $\text{5.8 Mbit/s}$ and for the downlink $\text{14.4 Mbit/s}$ $($i.e., significantly higher maximum values$)$, but these will probably not be achievable in practice.
- The third-generation mobile communications systems were to have greater bandwidth than the "GSM" already established at that time and sufficient reserve capacity to ensure high quality of service even in the face of constantly growing demands.
- In the development of the 3G systems, the "International Telecommunication Union" $\rm (ITU)$ has played an important role. Among other things, it created a catalog of requirements that defined their characteristics.
This catalog of requirements includes the following general conditions:
- High data rates from $\text{144 kbit/s}$ $($standard$)$ to $\text{2 Mbit/s}$ $($in-door$)$,
- symmetric and asymmetric data transmission $($IP services$)$,
- circuit-switched and packet-switched transmission,
- high speech quality and high spectral efficiency,
- seamless transition to and from second-generation systems,
- global reachability and distribution,
- applications independent of the network used $($virtual home environment$)$.
The IMT–2000 standard
In 1992, the "International Telecommuncation Union" $\rm (ITU)$ launched the $\text{IMT-2000}$ $($"International Mobile Telecommunications at 2000 MHz"$)$ standard to enable the above requirements. This comprises a number of different third-generation mobile communications systems that have been converged during the standardization process to enable the development of common terminals for all these standards.
In order to take into account nationally different preliminary work and to allow network operators to continue using existing network architectures to some extent,
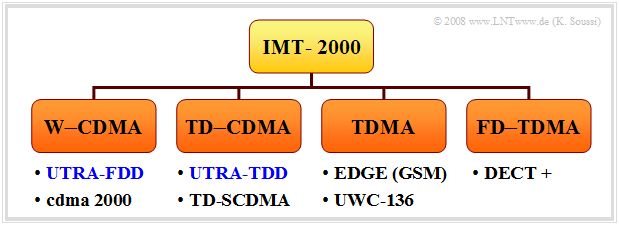
IMT–2000 includes several individual standards. These can be roughly divided into four categories:
- $\rm W\hspace{-0.12cm}-\hspace{-0.08cm}CDMA$: This includes the FDD component of the European UMTS standard as well as the American "cdma2000" system.
- $\rm TD\hspace{-0.08cm}-\hspace{-0.08cm}CDMA$: This group includes the TDD component of UMTS as well as the Chinese "TD-SCDMA", which is now integrated into the "UMTS–TDD" standard.
- $\rm TDMA$: A further development of the GSM off-shoot "EDGE" and its American counterpart "UWC-136", also known as "DS-AMPS".
- $\rm FD\hspace{-0.08cm}-\hspace{-0.08cm}CDMA$: The further development of the European cordless telephony standard $\rm DECT$ $($"Digital Enhanced Cordless Telecommunication"$)$.
In the following, we focus on the European-developed system $\rm UMTS$ $($"Universal Mobile Telecommunications System"$)$, which supports the first two standards "$\rm W\hspace{-0.12cm}-\hspace{-0.08cm}CDMA$" and "$\rm TD\hspace{-0.08cm}-\hspace{-0.08cm}CDMA$" of the IMT–2000 system family.
Historical development of UMTS
The following is some data on the historical development of UMTS and the techniques used. More information can be found, for example, at this "internet link".
- 1940-1950 First military applications of signal spreading techniques.
- 1949 First outlines of the CDMA process by C. E. Shannon and J. R. Pierce.
- 1970 Various CDMA developments for military systems, e.g. GPS.
- 1989-1992 Basic research on the characteristics of future mobile radio systems within the EU program RACE-1 $($Research, Analysis, Communication, Evaluation$)$.
- 1992 First consideration of the IMT-2000 standard by the ITU.
- 1992-1995 EU program RACE-2 focusing on "development of system concepts" - based on the results of RACE-1.
- 1996 Foundation of the UMTS Forum in Zurich - renaming of the planned European standard "W-CDMA" to "UMTS".
- 1998 Adoption of the two modes "W-CDMA" and "TD-CDMA" ' into the UMTS standard at the ETSI-SMG meeting in Paris.
- 1998 Establishment of the "3gpp forum" $($"3rd Generation Partnership Project"$)$ by the ETSI-SMG, T1P1, ARIB TTC and TTA committees.
- 1999 Adoption of the UMTS-R99 standard $($Release 1999$)$ by ETSI. This is considered the basis for the first available UMTS terminals.
- 2001 Adoption of Release 4 as a further development of UMTS-R99: "Quality of Service" $\rm (QoS)$ is now supported at the radio interface and in the fixed network.
- 2001 First commercial UMTS network of the Norwegian company "TELENOR".
- 2002 Adoption of UMTS Release 5: Architecture based on the GSM fixed network is replaced by a fully IP-based fixed network.
- 2002 First UMTS speech and data link from "Nortel Networks" and "Qualcomm". These companies are considered pioneers in the implementation of UMTS.
- 2004 Adoption of UMTS Release 6, a standard that provides improved QoS for the user and more effective resource management for the provider.
With UMTS, too, more than a decade has passed between the first conceptual considerations and the final introduction.
This was similar to the introduction of other communications systems, such as
- "ISDN" $($"Integrated Services Digital Network"$)$,
- "DSL" $($"'Digital Subscriber Line"$)$,
- "GSM" $($"Global System for Mobile Communications"$)$.
Frequency allocation for UMTS
The International Telecommunication Union $\rm (ITU)$ is responsible for allocating bandwidths and frequency bands for communications systems. In the case of UMTS in particular, however, there are discrepancies between the European and ITU frequency allocations, as some frequency bands were already occupied by other mobile communications systems in some countries.
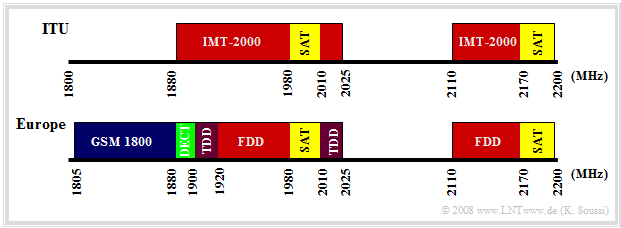
The graph shows the European $($bottom$)$ and the ITU frequency assignments $($top$)$. Meaning:
$\rm GSM \ 1800$:
Frequency band for the downlink of GSM 1800,
$\rm SAT$:
Satellite-based systems $($each $\text{30 MHz}$ for uplink and downlink$)$,
$\rm DECT$:
Digital Enhanced Cordless Telecommunications,
$\rm UTRA\:FDD$, for short: $\rm FDD$:
UMTS Terrestrial Radio Access – Frequency Division Duplex,
$\rm UTRA\:TDD$, for short: $\rm TDD$:
UMTS Terrestrial Radio Access – Time Division Duplex.
Note:
⇒ $\rm FDD$ consists of twelve paired uplink and downlink frequency bands of $\text{5 MHz}$ bandwidth each. The frequency bands are located in Europe between
- $\text{1920 MHz}$ and $\text{1980 MHz}$ in the uplink,
- $\text{2110 MHz}$ and $\text{2170 MHz}$ in the downlink.
⇒ $\rm TDD$ consists of five frequency bands of $\text{5 MHz}$ bandwidth each, in which both uplink and downlink data are to be transmitted using time division multiplexing.
- The TDD band lies between $\text{1900 MHz}$ and $\text{1920 MHz}$ $($four channels$)$ and between $\text{2020 MHz}$ and $\text{2025 MHz}$ $($one channel$)$.
- The band between $\text{2010 MHz}$ and $\text{2020 MHz}$ has not been licensed in 2007.
Full duplex
In order to separate the two transmission directions uplink and downlink, two different operating modes are supported in UMTS. A distinction is made between:
- »UMTS Terrestrial Radio Access Frequency Division Duplex« $\rm (UTRA\hspace{-0.08cm}-\hspace{-0.08cm}FDD)$,
- »UMTS Terrestrial Radio Access Time Division Duplex« $\rm (UTRA\hspace{-0.08cm}-\hspace{-0.08cm}TDD)$,
- The main difference between these two modes can be seen in the physical layer of the protocol stack.
- The two methods differ in both their duplex and multiple access methods.
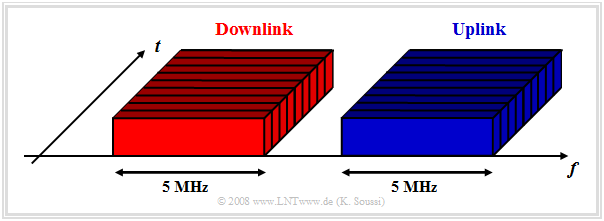
In the $\rm UTRA\hspace{-0.08cm}-\hspace{-0.08cm}FDD$ mode, as shown in the graph on the right:
- Uplink and downlink data are transmitted simultaneously on different but corresponding paired $\text{5 MHz}$ frequency blocks.
- Data from different subscribers are transmitted and received on the same frequency band.
- The use of different CDMA spreading codes enables the separation of the respective subscriber data.
- The TDMA method is also used to realize periodic functions such as power control.
- The FDMA method can be used in addition to CDMA and TDMA if the network operator has more than one frequency channel.
FDD mode is used only in Europe and mostly only for symmetrical services whose bandwidth requirements in the uplink and downlink are approximately the same. This is the case for speech communications or video telephony, for example.
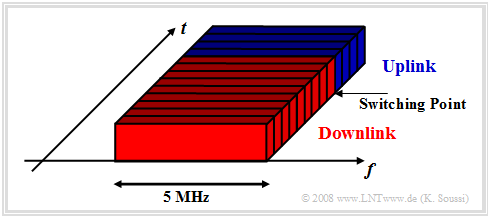
In the $\rm UTRA\hspace{-0.08cm}-\hspace{-0.08cm}TDD$ mode, uplink and downlink data are transmitted in the same frequency band. In this case, uplink and downlink are separated in time, as shown in the following diagram. Furthermore:
- The "switching point" can be flexibly selected depending on the data volume ratio between uplink and downlink.
- In TDD mode, the subscribers are identified both by the spreading code $($as in FDD$)$ and by the time slot.
- If the network operator has several frequency channels, FDMA can be used in addition to CDMA and TDMA as with FDD.
TDD mode was 2007 not used in Europe and, once introduced, will mainly be used for asymmetric services where the data volumes of downlink and uplink differ significantly.
Properties of the UMTS radio channel
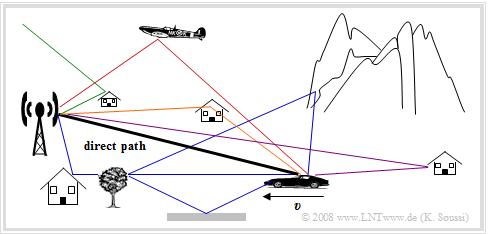
In the UMTS radio channel, in addition to interference from other subscribers and noise, a number of unpredictable, interfering and distorting effects occur, which also change over time.
⇒ Due to reflections as well as scattering and diffraction from objects, the transmitted signal experiences »multipath propagation«.
- The signal reaches the receiver not only via the direct path, but via several paths with different propagation times and different attenuation.
- The multipath scattering is influenced by the environment, but additionally also by a possible movement of the user, as indicated in the graph by the movement speed $v$.
⇒ The path loss goes back to propagation properties of electromagnetic waves – see page "common path loss model" in the book "Mobile Communication". For the study of this attenuation phenomenon, we assume a simplified path loss model. This states:
- The received power of a radio signal decreases with distance $d$ by $d^{-γ}$, where $γ$ is a medium-dependent constant of the radio propagation wave.
- Accounting for constructive or destructive ground reflections, the constant $γ$ below the "break point" $d_0$ takes values between $2$ and $3$.
- Above this characteristic point, the reflection effects increase and the propagation constant $γ$ grows to values between $3.5$ and $4$.
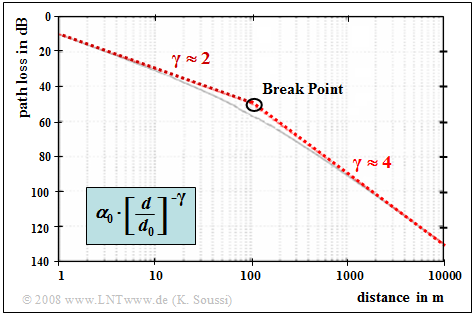
$\text{Example 1:}$ Shown on the right is the path loss $($in dB$)$ as a function of the distance $d$ $($in meter$)$.
In this example,
- the constant $α_0 = 10^{-5}$ is set ⇒ $10 \cdot \lg \ α_0 = 50 \ \rm dB$,
- the break point is at $d_0 = \ \rm 100 \ m$.
One can see from the graph:
- In the left-hand range $(d \ll d_0)$ holds $γ \approx 2$
- For $d \gg d_0$ on the other hand: $γ \approx 4$.
- In the region around $d = d_0$:
The propagation constant increases continuously from $γ = 2$ to $γ = 4$.
Frequency–selective and time–selective fading
An essential property of the mobile radio channel is the so-called »fading«. This is caused by time-varying shadowing and by possible movements of the mobile subscriber. In the book "Mobile Communications" this type of signal degradation is discussed in detail.
Here follows only a brief summary. One distinguishes on the one hand:
- »Short term fading« or "fast fading" ⇒ short term drops in the received power $($mostly in the microseconds range$)$.
- »Long term fading« or "slow fading" ⇒ only slow changes $($mostly in the seconds range$)$.
- Fast fading mainly affects systems with large symbol durations, i.e. small bandwidths. However, since the bandwidth of UMTS is much larger than that of GSM, this system is less susceptible to fast fading.
Furthermore, fading can also be classified as follows:
- »Frequency-selective fading« is caused by multipath propagation over paths with different delay times.
As a result of this fading, different frequency components are attenuated differently by the power transfer function $|H_{\rm K}(f)|^2$ of the channel.
- »Time-selective fading« occurs due to a relative motion between transmitter and receiver.
This causes frequency shifts depending on the direction of movement $($towards or away from the transmitter$)$ which are physically described by the "Doppler effect".
- The fading characteristics "frequency selective" and "time selective" shall now be explained in more detail, in particular it will be explained under which conditions which of these fading types are to be expected. At this point we also refer to two e-learning tools:
- HTML5/JavaScript applet "The Doppler effect",
- German language SWF applet "Multipath propagation and frequency selectivity".
- The fading characteristics "frequency selective" and "time selective" shall now be explained in more detail, in particular it will be explained under which conditions which of these fading types are to be expected. At this point we also refer to two e-learning tools:
$\text{Characteristics of frequency-selective fading:}$
- Receiving different scattering components with different delay times results in a »delay spread« $T_{\rm V}$, defined as the difference between maximum and minimum delay times $($ German: "Verzögerungszeiten ⇒ subscript "V"$)$. The inverse of this gives approximately the »coherence bandwidth« $B_{\rm K}$.
- It is called "frequency-selective fading" if the coherence bandwidth $B_{\rm K}$ is much smaller than the signal bandwidth $B_{\rm S}$. As a result, different frequency components are attenuated differently by the channel, resulting in linear distortions.
$\text{Characteristics of time-selective fading:}$
- In "time-selective fading", a so-called »Doppler spread« $B_{\rm D}$» occurs, which is defined as the difference between maximum and minimum Doppler frequencies.
- The reciprocal of which is called the "correlation time" $T_{\rm D} = {1}/{B_{\rm D} }$. In some literatures, this quantity is also referred to as "coherence time". In UMTS, "time-selective fading" occurs whenever the correlation time $T_{\rm D}$ is much smaller than the chip duration $T_{\rm C}$.
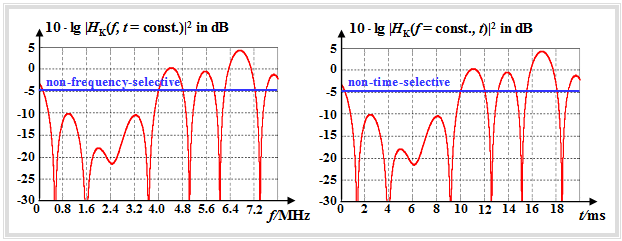
$\text{Example 2:}$ The left graph illustrates the difference between frequency-selective and non-frequency-selective fading:
- Shown in this graph is the logarithm power transfer function $\vert H_{\rm K}(f,\ t)\vert ^2$ of the channel at a fixed time $t$.
- While non-frequency-selective fading is plotted in blue with $-5 \ \rm dB$ , the red curve shows an example of frequency-selective fading.
- Different frequency components are thereby attenuated differently.
The right graph shows schematically "time-selective fading":
- Here, the power transfer function $\vert H_{\rm K}(f,\ t) \vert ^2$ of the channel for a fixed frequency $f$ is plotted.
- The blue curve is valid for non-time-selective fading: At any time the signal is attenuated by $5 \rm dB$ .
UMTS services
One of the goals of the introduction of UMTS is to expand and diversify the mobile communications services offered. A UMTS capable terminal must support a number of more complex multimedia applications and functions in addition to the classic services $($speech transmission, messaging, ...$)$.
These services can be divided into six main categories, depending on the application:
- Information : Internet surfing $($info-on-demand$)$, online print media,
- Communication: Video and audio conferencing, fax, ISDN, messaging,
- Entertainment: Mobile TV, mobile radio, video-on-demand, online gaming,
- Business: Interactive shopping, e-commerce,
- Technical area: Online support, distribution service $($speech and data$)$,
- Medical area: Telemedicine.
Security aspects
The security features in UMTS networks are based on the same principles as in GSM. However, some GSM security features have been removed, replaced or expanded.
This has made
- the encryption algorithms more robust,
- the authentication algorithms more stringent, and
- the subscriber confidentiality criteria tighter.
The main security standards adopted from GSM in UMTS are:
- subscriber authentication,
- confidentiality of the subscriber identity,
- encryption of the radio interface.
In addition to these, other security measures have been observed in UMTS:
- Mutual authentication to avoid the use of false base stations,
- encryption of the connection between base station and associated control node,
- encryption and authentication of security data during transmission,
- mechanisms for updating the security features.
One can classify the above security measures according to the graph. A distinction is made between security concepts for
- the »Network Access Security« for each subscriber,
- the »User Domain Security « – access to terminal equipment is ensured,
- the »Network Domain Security« – a secure exchange of control data between nodes within the network domain is ensured,
- the »Application Domain Security« – the secure exchange between applications of the subscriber terminals and the network providers is guaranteed.
The UMTS subscriber can see at any time which of these security measures are in operation and which of them are required for specific services. In this context, one speaks of "Visibility and Configurability Security".
Exercises for the chapter
Exercise 4.1: Different Duplex Methods for UMTS
Exercise 4.2: UMTS Radio Channel Basics